 |
|---|
Version March 2005
 |
|---|
by vvf
Following a link posted by elody on the Seeker's messageboard (http://fravia.2113.ch/phplab/mbs.php3/mb001) I came across a very interesting anonymity tool, interesting if a bit controversial, as will become clearer somewhere down the line in this brief essay.
What is TOR?
In the own words of the Electonic Frontier Foundation:
Tor is a network of virtual tunnels that allows people and groups to improve their privacy and security on the Internet. It also enables software developers to create new communication tools with built-in privacy features. Tor provides the foundation for a range of applications that allow organizations and individuals to share information over public networks without compromising their privacy.
Individuals can use Tor to keep remote websites from tracking them and their family members. They can also use it to connect to resources such as news sites or instant messaging services that are blocked by their local Internet service providers (ISPs).
Groups such as the German "Diabetes People" organization recommend Tor for safeguarding their members' online privacy and security. Activist groups like the Electronic Frontier Foundation (EFF) are supporting Tor's development as a mechanism for maintaining civil liberties online. Corporations are investigating Tor as a safe way to conduct competitive analysis, and are considering using Tor to test new experimental projects without associating their names with these projects. A branch of the U.S. Navy uses Tor for open source intelligence gathering, and one of its teams used Tor while deployed in the Middle East.
The variety of people who use Tor is actually part of what makes it so secure. Tor hides you among the other users on the network, so the more populous and diverse the user base for Tor is, the more your anonymity will be protected.
How Does it Work?
EFF info again:
Tor is an implementation of version 2 of Onion Routing. In brief, Onion Routing is a connection-oriented anonymizing communication service. Users choose a source-routed path through a set of nodes, and negotiate a "virtual circuit" through the network, in which each node knows its predecessor and successor, but no others. Traffic flowing down the circuit is unwrapped by a symmetric key at each node, which reveals the downstream node.
Basically Tor provides a distributed network of servers ("onion routers"). Users bounce their tcp streams (web traffic, ftp, ssh, etc) around the routers, and recipients, observers, and even the routers themselves have difficulty tracking the source of the stream.
So far, there is nothing revolutionary in its design. What is worth noting is that TOR presents a few advantages compared to commercial tools: it is free, open source (well, kind of anyway), easy to install and easy to use. As I discovered while experimenting with it, it is also reasonably fast for what is basically a chain of encrypted proxies. Its main purpose is to provide anonymity and privacy on the web, and I will show you how you can use it together with Opera, the Proxomitron and SocksCap on Windoze, should you need to go places that you don't want your ISP or (almost :) anybody else to know, staying anonymous enough for most purposes.
Just as a reminder, anonymity in this context is when the web sites you're browsing don't know who you are and where you're coming from, while privacy is when even your own ISP doesn't know what sites you visit, what searches you make or what generally is of interest to you.
I installed and tested TOR on one of my boxes running XP SP2, Opera/Firefox and the Proxomitron. TOR also works on Mac and GNU/Linux, just so that you know. Now, as Windows is no Linux, you also need to download and install SocksCap for this whole thing to work properly, and then make sure you've got Proxomitron's SSL libraries at hand because you will need them too (SSL provides encryption, link given somewhere below).
Here are the steps, don't let them scare you, it's quite easy:
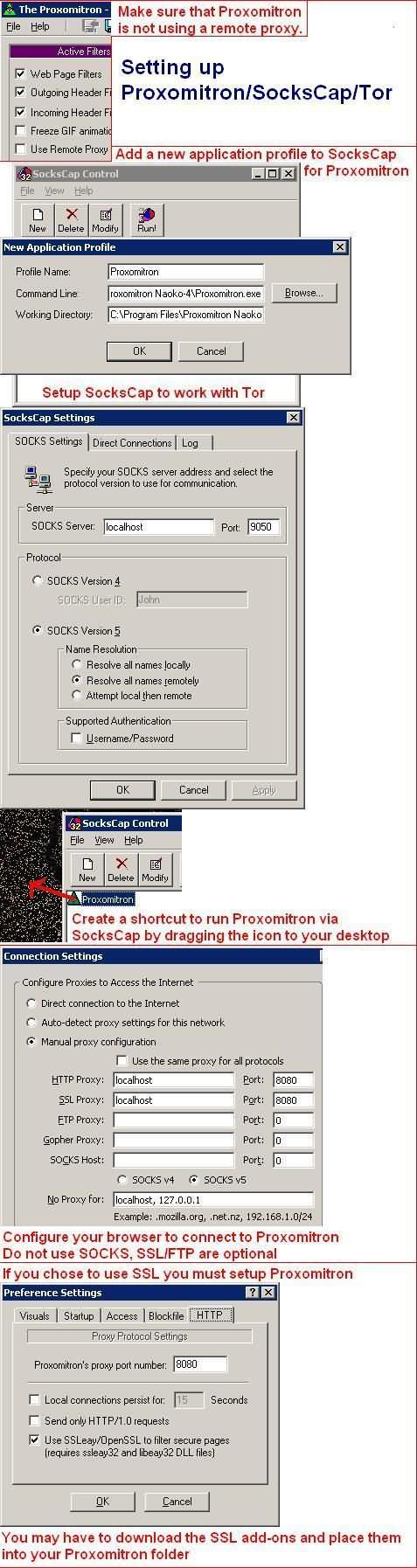
For ssl, which I advise you to try, the files you will need to unzip and place in Proxo's folder are in here:
You are now ready to experiment! First, close the Proxomitron if it is running and double-click on the Proxo link created on your desktop. The Proxo is back, and now it will run through SocksCap. Run TOR; a black dos-like box will open and that will be all, no graphical interface (not needed anyway). Now open Opera and go to whatsmyip. That's not your usual IP, is it? ;-)
You will notice that browser requests made within one minute will show the same IP, then the IP changes randomly, and so on.
You can do more testing here, here and here.
Just hit reload after some time and enjoy the fun.
I have spied on my browser with Ethereal, a packet sniffer, by launching a simple Google query in Opera ("qwerty") and checking if the sniffer finds either "qwerty" or "google" or Google's IP in the strings sent by my browser to the world at large. As you can imagine, I found all these and more when using the plain Opera + proxo combination. Had I used a web proxy it would have been the same: these strings are "in clear" between my browser and my ISP.
When using TOR, all the sniffer can see is one or two "node" addresses and no other info, because it's all encrypted. These nodes are where TOR connects first, then the packets go encrypted through other nodes until they reach their final destination.
In this way, you can be anonymous (with respect to your target web sites) and at the same time enjoy privacy (with respect to your ISP).
Then, if you played enough and feel like going back to non-anon mode, just shut down the 'sockscapped' Proxo and TOR and start your plain old Proxo from its usual location.
Finally, the controversial bit. You should know that, before going open source, this system was initially developed by the US NAVY (you may remember the now extinct "Onion Router"). Currently, TOR is used by the Navy and who knows what other agencies, if you remember the EFF quote I mentioned earlier: a branch of the U.S. Navy uses Tor for open source intelligence gathering, and one of its teams used Tor while deployed in the Middle East recently.
Although its source is available, TOR is Copyright (c) 2001-2004 Roger Dingledine, Copyright (c) 2004-2005 Roger Dingledine, Nick Mathewson. According to the online CV that he has published, Mr. Roger Dingledine has been employed, among others, by the NSA. You can read his detailed technical presentation of the TOR system at Defcon 12 Speakers (2004, Las Vegas) right here: Dingledine
You have been warned :)
Nonetheless, I hope that you will find all this both useful and enjoyable.
Further info: